How to Identify Which Code Was Used to Encrypt
Encryption has been used for many thousands of years. If you are interested in HTTPS.
Best Ways To Encrypt Passwords Keys More With Php In 2022
It supports over 220 unique hash types using regular expressions.

. 9 times out of 10 they are using some sort of API for the hashingsaltingencryption and you can imitate or reverse it using the same API. Give our encryptdecrypt tool a try. Find the code to learn whats happening here.
But this for identifying the kind of encryption technique and its from 2014 dont know if that is still valid. The possibilities become very numerous without a way to precisely identify the encryption. The command would look like this.
Now click on More Information. It is able to identify a single hash parse a file or. Hashes usually use a hexadecimal or base64 charset.
How to identify Encryption algorithm for data coming in fieldattribute values of an xml. Encrypt or decrypt any string with just one mouse click. Furthermore nearly all messages can be stored in binary identifying the encryption precisely is difficult.
Plain text password etc As mentioned above base64 is often used to encode the binary result of encryption or hashing. When this is the case you must be able to understand the inner workings of encryption algorithms to be able to identify code. Another thing I just want make sure that the field is encrypted dont want to identify the encryption technique.
If you use someone elses public key to encrypt the data only that person will be able to read the data. Encryption uses an algorithm to scramble or encrypt data and then uses a key for the receiving party to unscramble or decrypt the information. - 1 Bpo9ttg6 sWupAOzq1LrawrmDUBwPE0 Bpo9ttg6 is the salt and sWupAOzq1LrawrmDUBwPE0 is the hash.
While testing an application there are some keywords that will quickly help us in identifying classes algorithm used for the encryption. The message contained in an encrypted message is. Password Encryption Alone Isnt Enough With the use of hashing codes and salt you can protect your password at rest and in transit.
Cryptography is the discipline of using codes and ciphers to encrypt a message and make it unreadable unless the recipient knows the secret to decrypt it. Codes Ciphers Encryption and Cryptography. Although it can be a little tricky when the code is obfuscated.
You can use encryption for yourself to experiment with but you should not trust your own code to provide proper security. It is composed of few distinct characters a binary message containing only 0s and 1s has a low entropy. For added security you can select this then youll have to create a new password and share it with the person whom you send the file and only the person who has this password will be able.
This is very unique code decrypter tool which helps to decrypt data with different encryption algorithms. By simply uploading a ransom note andor an encrypted file preferably both for best results the site will use several techniques to help identify what ransomware may have encrypted the files. If a hash has dollar signs in it this is usually a delimiter between the salt and the hash.
Somewhere in there the passwords are undergoing a cryptographic operation. Hash Identifier or HashID is a Python-based tool that allows you to quickly identify types of hashes used to encrypt passwords. But I think you are encrypting the file using cryptography so SystemIOFileGetAttributes will not work.
Modes supported such as CBC cipher block. Modern definition of security uses the concept of indistinguishability. This will describe the version of TLS or SSL used.
The expectation that base64 decoding is the only step necessary to get back the original eg. The following codes and ciphers can be learned and used to encrypt and decrypt messages by hand. It supports various Algorithms such as ArcfourBlowfishBlowfish-compatCast-128Cast-256DesGostLoki97Rc2Rijndael-128Rijndael-192Rijndael-256SaferplusSerpentTripledesTwofishXtea.
Your absolute best bet is to get a copy of the code that is used to store the passwords. Doing encryption correctly is not easyIt involves reading and learning a lot. In fact experts say that a strong encryption policy can leave you with blind spots.
Right Click Folder - Properties - General Tab - Advance Button - CheckBoxes in Compress and Encrypt Attributes groupbox. The message has a low entropy. Encrypt with a password.
This is a very basic example but we do not want anyone to get at our source code. But you wont achieve full security until you do a little bit more. There are times however where the encryption is statically compiled into the malware or even a custom written encryption algorithm is used.
If you want to use encryption in a product that is to be used by other people or even companies please ask an expert to review it as a consultant. One typical use case is to base64 encode the result of encryption or hashing which both create binary results. Look for the Technical details section.
Encrypt decrypt crypt AES DES SecretKeyFactory secretKey Cipher InvalidKeyException etc. You think youre secure when youre not. In the address bar click the icon to the left of the URL.
Somewhat similar to HashTag Password Hash Type Identification Identify Hashes - which we posted about a while back. We also dont want anyone to run this code after 1 hour so when we encrypt the file we can enforce an expiration time of 1 hour from now with the --ttl option and we can delete the plaintext py file after encryption by adding the --remove option. Even if you know which cipher has been used and you have access to a large set of pairs plaintextciphertext using the same key as large as you wantcan handle if you are presented with a pair of two messages one of them being a ciphertext and the other is a random sequence of bits the fastest way to.
Select the Security tab.

How To Encrypt Strings Files In Your Source Code Dev Community
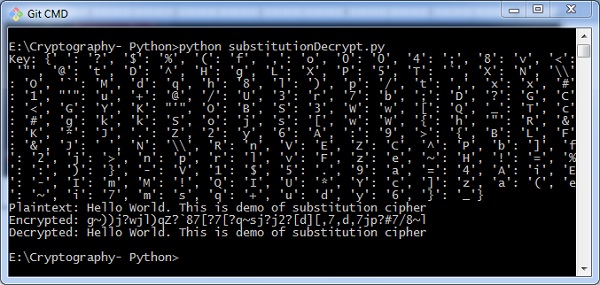
Cryptography With Python Quick Guide
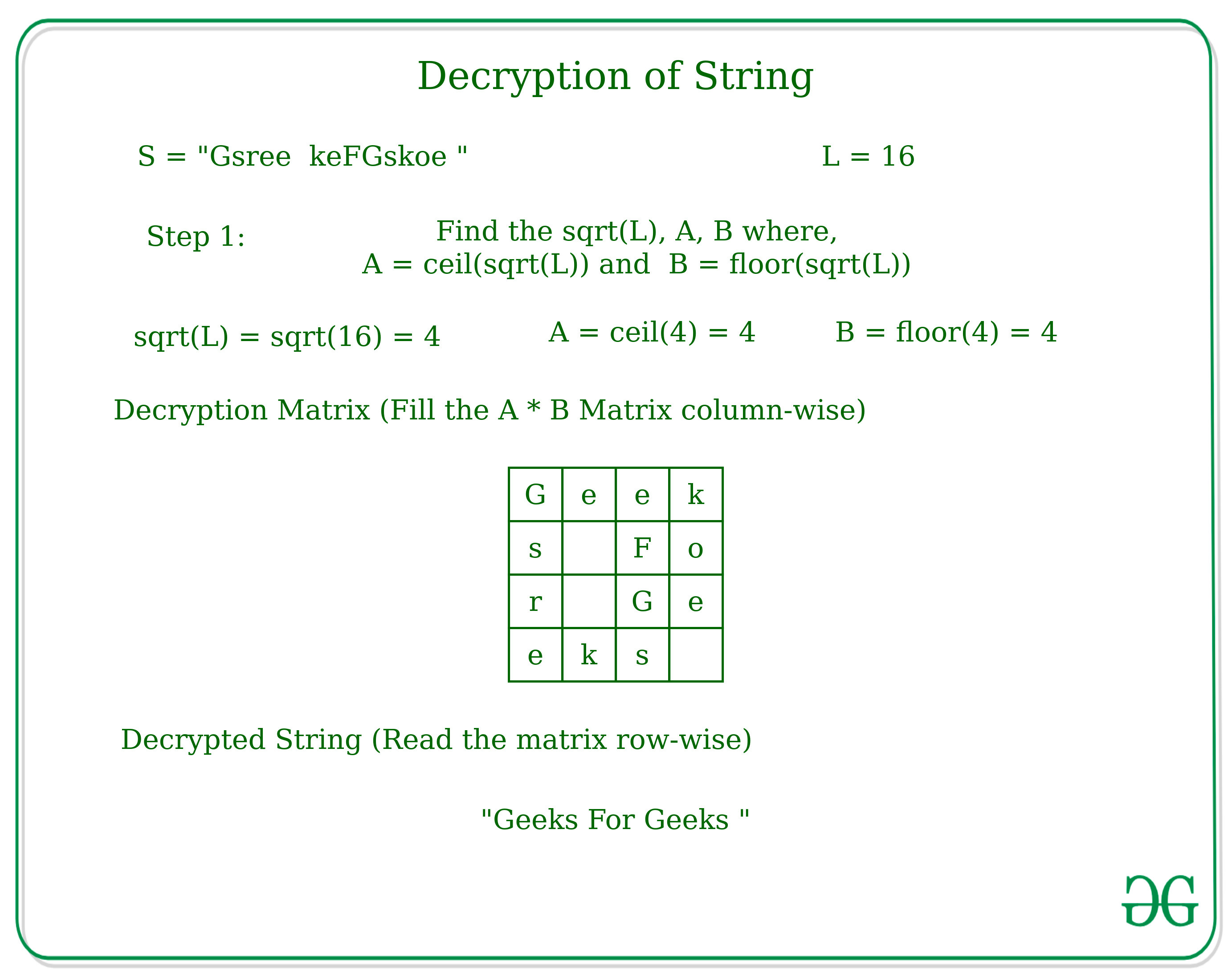
Encryption And Decryption Of String According To Given Technique Geeksforgeeks

What Is Encryption Types Algorithms Practices Proofpoint Au
C Program To Encrypt And Decrypt The String Source Code Explained

Encrypt Strings Files Directly In Visual Studio Code Editor By Bartosz Wojcik The Startup Medium
A Encoding Data In Qr Codes B Encrypting And Then Encoding Data In Download Scientific Diagram
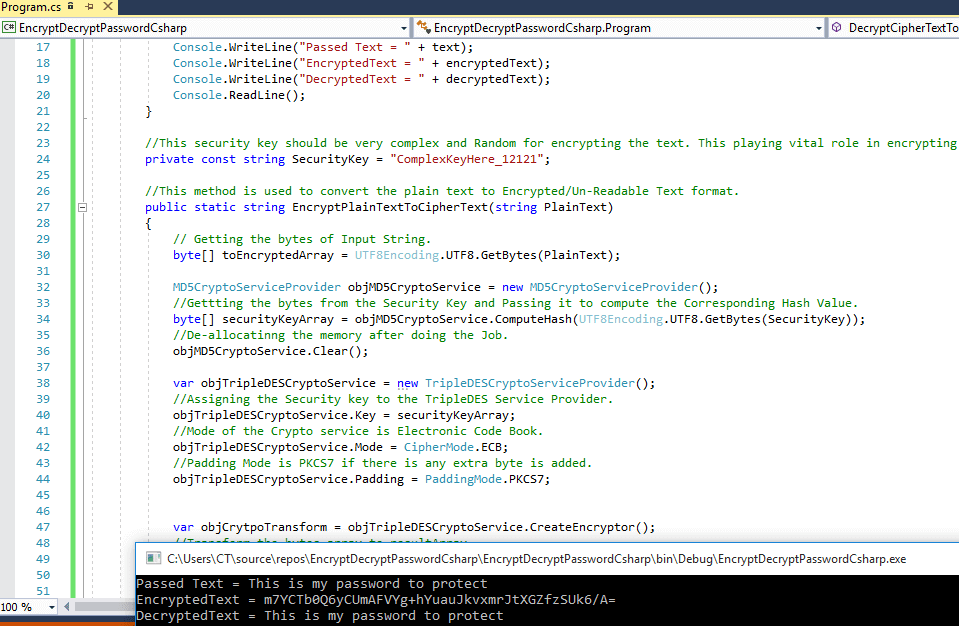
C Encrypt Password Decrypt It C Console Application Example Qa With Experts
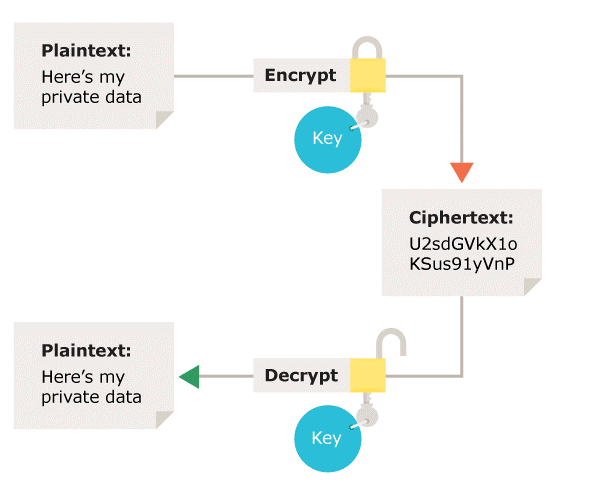
What Types Of Encryption Are There Ico

The Display Of The Jpg File Binary Code Before Encrypted After It Is Download Scientific Diagram

Code Encryption An Overview Sciencedirect Topics

Encryption 101 Decryption Tool Code Walkthrough Malwarebytes Labs
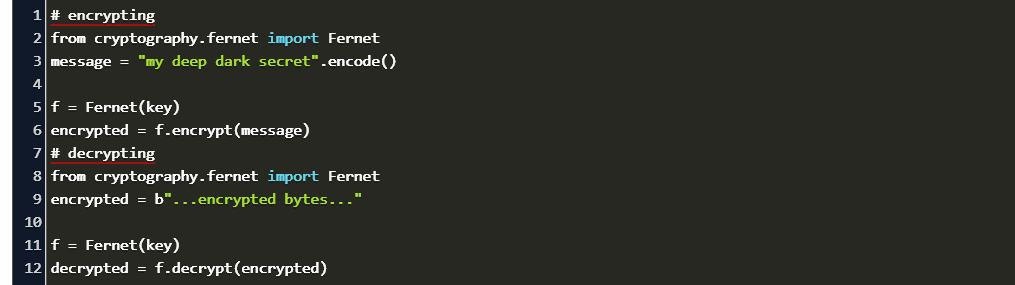
Encrypt And Decrypt Python Code Example

How To Encrypt Strings Files In Your Source Code Dev Community
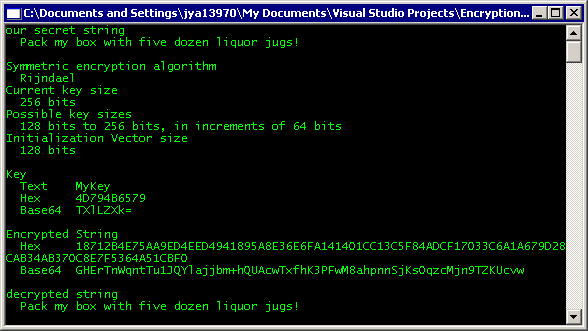
Net Encryption Simplified Codeproject

5 Common Encryption Algorithms And The Unbreakables Of The Future

Encryption And Decryption In Php Example Code Example

Encrypt Php Source Code And Php Obfuscation Solution
C Program To Encrypt And Decrypt The String Source Code Explained
Comments
Post a Comment